A framework for global trust and identity
Trusted identity management is crucial for global research collaboration.
To increase global collaboration, we’re building on an international Trust and Identity Framework. The AAF is currently working with the national research infrastructure community to apply this international framework to the Australian context.
In response to a need for secure research collaboration, the EU’s Horizon 2020 project developed a Trust and Identity Framework consisting of a technical Blueprint Architecture and a Policy Development Kit, that is now widely used by national research infrastructure in Europe and the USA.
The Authentication and Authorisation for Research Collaborations (AARC) Blueprint Architecture provides a technology neutral blueprint, along with a shared suite of policies that standardises the implementation of access and authorisation infrastructure for research communities.
Who uses the AARC Framework?
The AARC Framework has been adopted internationally by many earth sciences, life sciences, astronomy, high energy physics, the arts, and humanities research institutes. Australian researchers regularly collaborate with these facilities and a consistent approach to authentication and authorisation infrastructure will support ongoing collaboration.
Institutes that have adopted the AARC Framework include:
A Trust and Identity Framework consists of Technology and Policy
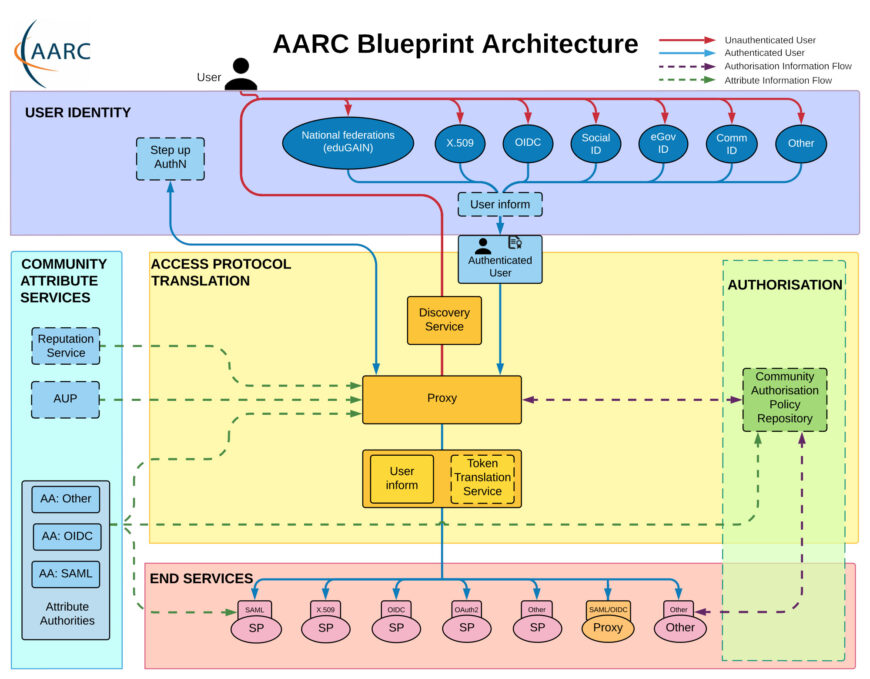
Blueprint Architecture
The technical architecture is a set of software building blocks that can be used to implement federated access management solutions for national and international research collaborations. It is a customisable and secure solution that can be tailored to a research institute's needs.
Policy Development Kit
Accessing, using, and operating services for research is inherently distributed. The question of trust for users, resource providers, and infrastructures, is a key concern. A set of policy documents has been created to develop a shared understanding of this trust. These policies outline the operational measures undertaken by the infrastructure to properly provide services and principally cover security measures, user management and data protection.
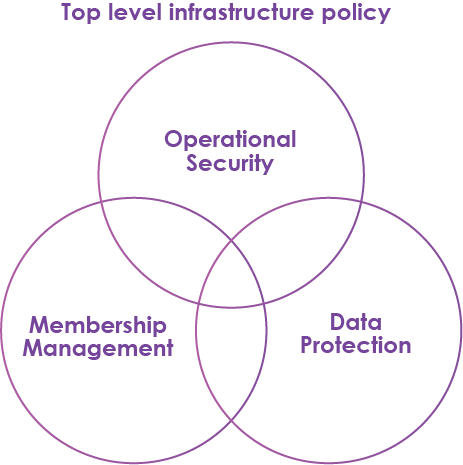
Each organisation or service may already have their own policies or be informed by the policies of their host institutions, on how privacy and data are managed. These policies are not designed to replace them, they are designed to become the baseline for all infrastructure in a collaborative research environment, and build a layer of common trust between users and the infrastructure community.
Applying the Framework to Australian research infrastructure
Software Toolkit
Discover an introductory suite of software that align with the Trust and Identity Framework, to enhance your national research infrastructures trust and identity capability. These software examples are currently being explored by the research community to implement trust and identity for their organisation.
Policy Development Kit
In collaboration with the national research infrastructure community through a Policy Working Group, we are currently developing a shared understanding of policies required for trusted access to infrastructure for the Australian context.
These policies and documents outline the operational measures required by an infrastructure to properly provide services and cover security measures, user management and data protection for research collaboration across facilities and will form a Policy Development Kit.
